Maintaining Cybersecurity under Rapid Change at Your Institution
Former Analyst
![Cybersecurity-TTG-TopOfMind-750x350[1]](https://www.thetambellinigroup.com/wp-content/uploads/2018/03/Cybersecurity-TTG-TopOfMind-750x3501-1.jpg)
The proliferation of Bring Your Own Device (BYOD), cloud computing, shadow IT, and the Internet of Things (IoT) is directly impacting enterprise computing systems and how higher education institutions respond to change. Institutions now must operate with the boundaryless data center, as every faculty and staff member, student, and guest carries a computer in their pocket. Further, The Tambellini Group research shows that institutions are moving to hybrid local-cloud computing enterprise architectural models. Walled off data centers and servers, strictly managed by IT departments, are remnants of the past. These factors all combine to create an attack surface that is constantly expanding. Keep reading to explore the issues that arise in maintaining security in a changing computing environment, particularly as institutions work to implement or maintain a defense-in-depth strategy. I’m going to argue for a shift from the traditional defense-in-depth model to a zero-trust model, and we welcome your comments!
The trends outlined above require an agile security posture, and the traditional framework of defense-in-depth must evolve. The National Security Agency (NSA) developed defense-in-depth, with controls that span physical, technical, and administrative areas (Wikipedia n.d.). At the core of defense-in-depth is a multi-layered approach to security controls with the intent to increase security of the IT system as a whole If an organization has a defense-in-depth strategy, in the event of “an attack [that] causes one security mechanism to fail, other mechanisms may still provide the necessary security to protect the system” (OWASP n.d.). This table from the NSA outlines examples of layered defenses. (National Security Agency n.d.)
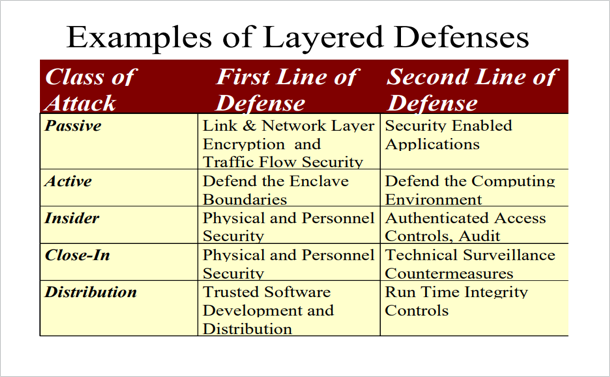
Unfortunately, defense in depth is difficult and costly to maintain in a computing environment that is undergoing continual changes. Repeated corporate and governmental data breaches (even within organizations like the U.S. Office of Personnel Management, which had deployed a defense-in-depth strategy) demonstrate the need for a new approach to security.
A zero-trust model is the most viable framework to secure your assets; however, it is not inexpensive to implement. Google developed the BeyondCorp security model based on zero-trust, and it “shifts access controls from the network perimeter to individual devices and users” (Google n.d.). At its core, the zero-trust model provides people and device security.
Zero-trust reimagines traditional identity and access management (IAM). (Look for Tambellini’s upcoming reports on IAM in spring 2018.) Ping Identity goes so far as to claim that “identity is the new perimeter” (Ping Identity 2017). The main components of zero-trust are all about managing identities and access. Zero-trust redefines the computing “identity” to mean a user plus device at any given point in time. Zero-trust forces authentication, uses granular access controls, and monitors device state before allowing access to any systems. A zero-trust strategy may include multi-factor authentication, federated single-sign-on, and proxy servers. Zero-trust also requires robust patch management, asset management, and vulnerability scanning (Osborn 2016).
We can further examine the role of a zero-trust model by applying it to IoT devices. Zero-trust becomes critical with IoT because it can be implemented to enforce how and when you allow those insecure devices to communicate with enterprise systems. Zero-trust gives the institution the ability to dynamically respond in real time to new users and devices attempting to access critical systems. Multiple identity and access management vendors are already providing solutions to tackle this capability.
If we combine the rise of IoT with the trend towards hybrid enterprise architectures, the need for zero-trust becomes even more evident. Zero-trust enforces a policy of never trusting any user/device attempting to access an asset, and it demands continual verification of the user/device. All resources must be accessed securely, regardless of location (i.e., whether the resource is in the cloud or on-premises).
Zero-trust is not without its challenges. To implement a zero-trust model, an organization must have a well-funded, highly-skilled staff who understand access rights across the entire organization. Every piece of the technology stack has to be mapped. In a cloud-computing environment (and don’t forget shadow IT), this becomes very difficult. Zero-trust requires constant monitoring, care, and feeding to be maintained properly. It also requires significant investments in technologies that not all institutions can afford.
Though zero-trust is difficult to implement, Google has shown it is possible. Google has spent seven years perfecting the model and has further provided guidelines and thorough documentation of their work so that other organizations might follow their example. Google’s “Migrating to BeyondCorp: Maintaining Productivity While Improving Security” outlines exactly how an enterprise can move to a similar zero-trust model, and it describes the potential impact on the enterprise and its employees (Jeff Peck 2017). Wide adoption of this model will require time, cultural shifts, and significant investments, but the flexibility it provides has the potential to help protect an institution’s most sensitive assets, even amid changing computer systems. Has your organization considered moving towards zero-trust?
We all know that funding and staffing to implement this type of program are hard to come by in higher ed. That’s why The Tambellini Group is announcing our new CISO Advisory services. Be on the lookout for more to come on this exciting new offering; we are committed to helping higher education institutions manage their risk affordably!
Categories
Share Article:

Other Posts From this Author:
© Copyright 2025, The Tambellini Group. All Rights Reserved.